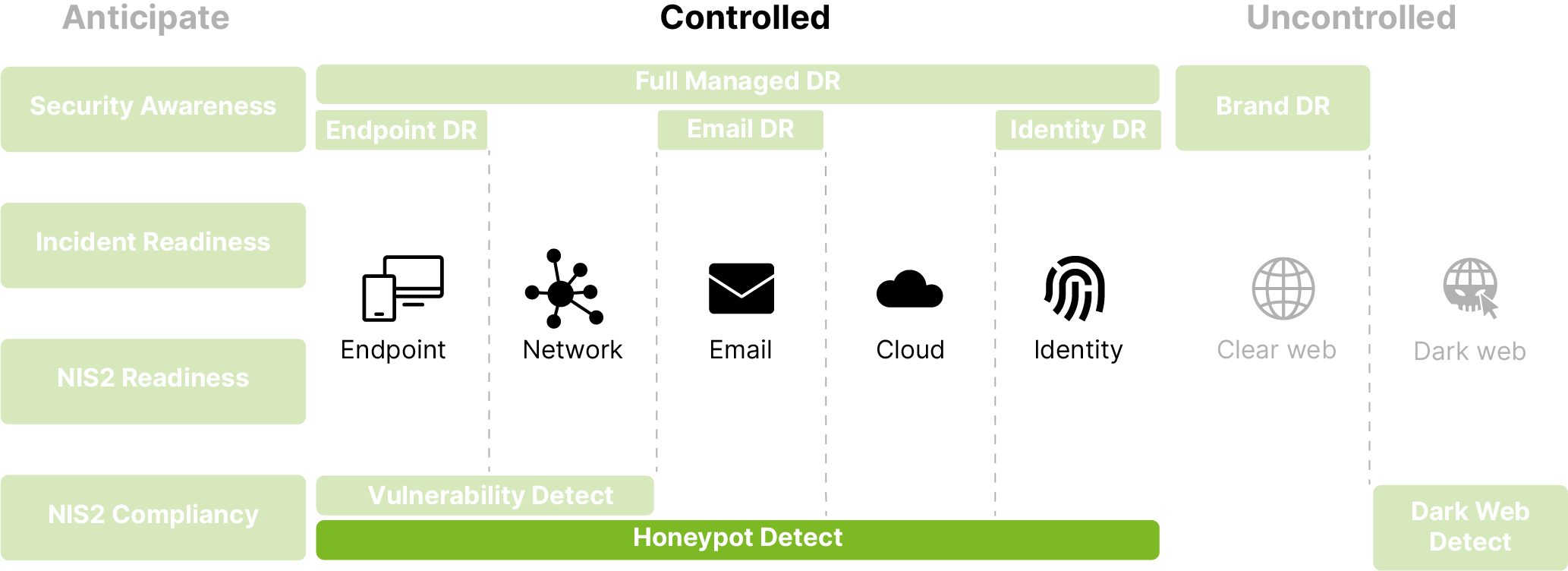
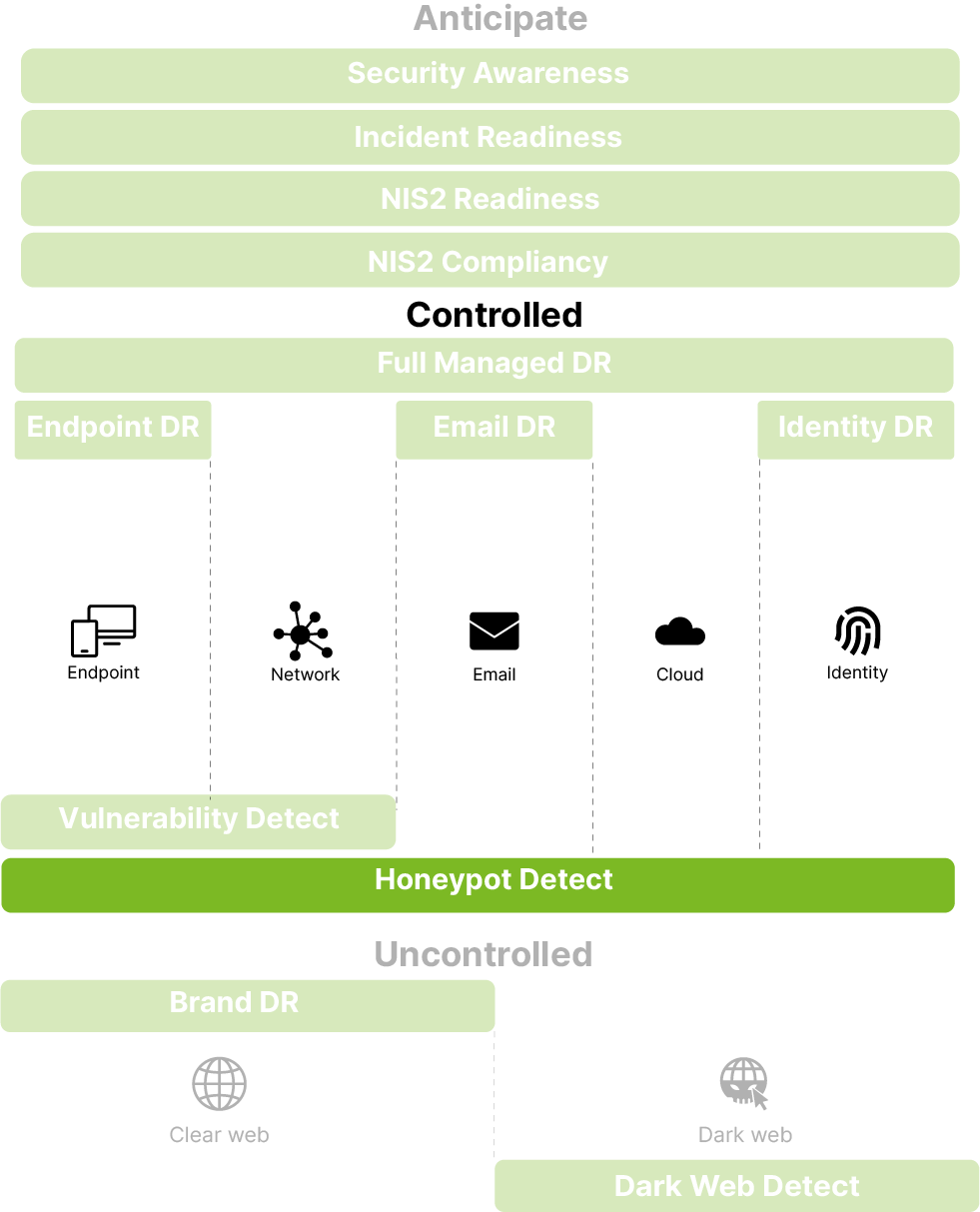
Honeypot Detect
Netleaf’s Honeypot Detect is a cybersecurity solution designed to identify unauthorised access attempts by presenting attackers with fake, high-value targets. By strategically deploying honeypots such as decoy devices, QR codes, API keys, and documents, we can divert malicious actors’ attention and trigger alerts upon interaction, enabling swift detection and response.
Why choose our Honeypot Detect
Our Honeypot Detect service offers comprehensive protection and support:

Local expertise
Our in-house analyst speak your language and work closely with your team.

Around the clock security
24/7 monitoring and critical alert handeling to keep your systems protected at all times.

Quarterly review, reporting, and meetings
Stay engaged with regular updates about the platform and the alerts we’ve identified. These sessions provide an opportunity to discuss findings, address concerns, and ask questions about your security environment.

Up to 10 honey tokens
Customise your protection with up to 10 honey tokens for each licensed honeypot.

Incident response channel
In the event of a breach, you can count on us to provide expert guidance and take swift action to support you.
How we do it
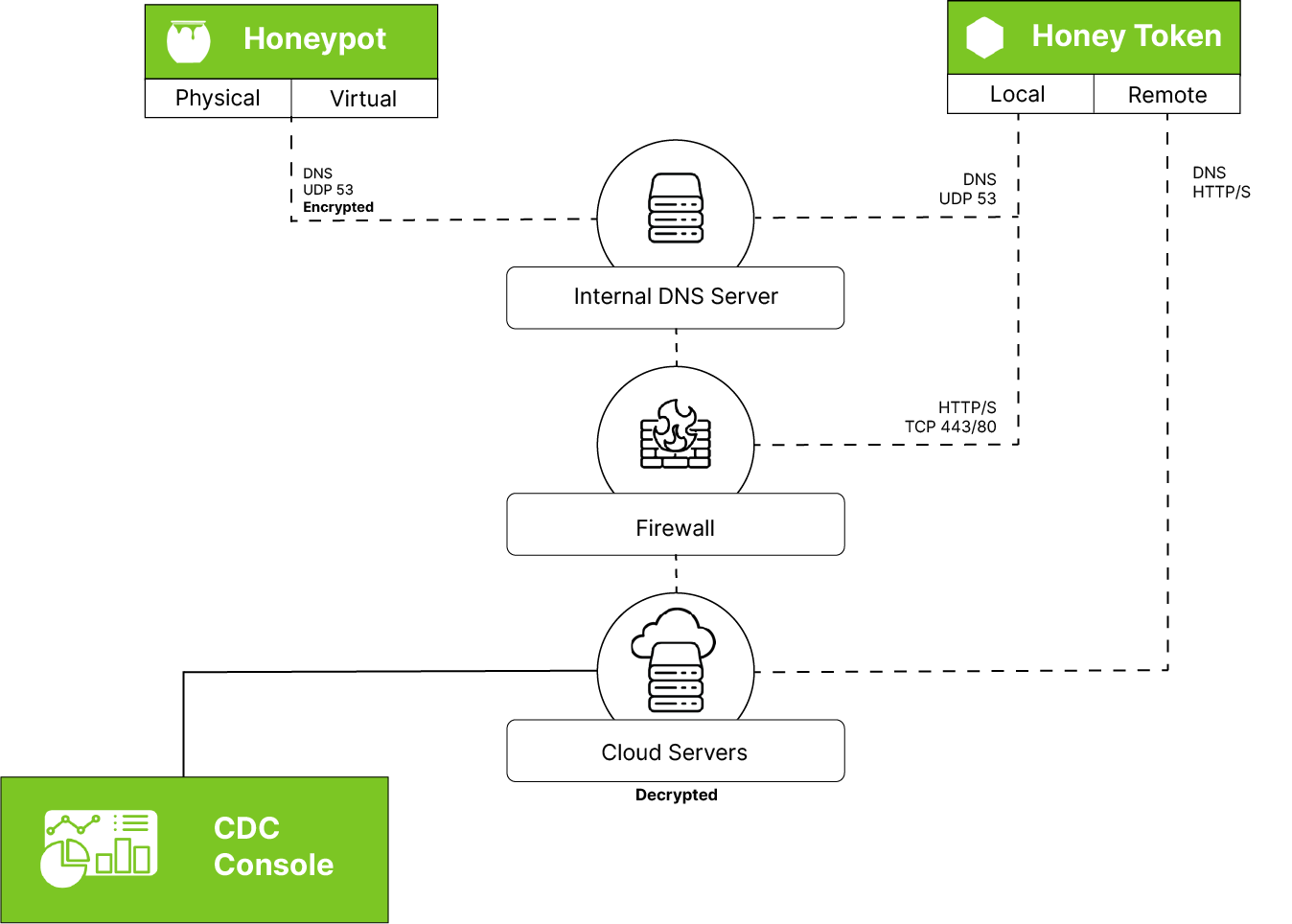
Honeypot decoys are strategically placed within your internal network to mimic real assets, luring potential attackers while remaining undetectable to legitimate users. These decoys securely communicate with our cloud-based management server via DNS, encrypting all traffic.
Beyond device-based honeypots, our deception technology includes virtual honey tokens designed to detect unauthorised access attempts to applications, credentials, folders, files, and more. Depending on the token type and client location, communication occurs over either HTTP/S or DNS.
Since our solution leverages standard DNS and HTTP/S network communication flows, no changes to firewall or network configurations are typically required for cloud connectivity, ensuring a seamless and non-intrusive deployment.
The moment an attacker or unauthorised entity interacts with a decoy, our Cyber Defence Centre (CDC) is immediately alerted. Our security analysts promptly investigate the event and notify you if urgent action is required. If necessary, you can engage our Incident Response (IR) team for deeper threat analysis and expert guidance on mitigation and resolution.
How it works
Our Honeypot Detect service offers comprehensive protection and support:
Intrusion detection through honeypots & tokens
Honeypots and tokens serve as deceptive traps, enabling the detection of attackers who have evaded traditional defences. By engaging with these deceptive traps, unauthorised activity is detected early.

High accuracy with minimal false positives
Our security specialists work closely with you to determine the optimal deployment of honeypots and tokens, ensuring minimal false positives.

Fast setup and deployment
Pre-configured decoy templates for Windows, Linux, macOS, and network services, along with network communication between the decoy devices and the cloud management server using DNS, enable rapid deployment customised to your environment.

Extensive notification capabilities
We ensure you’re promptly informed of all noteworthy activity based on agreed-upon communication protocols. Additionally, you have the option to automatically forward alerts via syslog, email, or webhook.
Immediate value
With no required baselining period and a straightforward setup, you gain immediate security benefits.
Protect your organisation today
Honeypot Detect serves as a critical last line of defence against advanced cyber threats, alerting you when other preventive security measures have failed. By identifying malicious activities targeting decoy assets, you gain valuable insight into potential risks and attacks in progress. For a comprehensive overview of our full defence strategy, including proactive measures and monitoring, visit our Cyber Defence Center.
Contact us today to learn how Honeypot Detect and our broader cyber security solutions can strengthen your security posture.
